As Legal Counsel, you are a key player in your company’s data protection processes. Whether you work alone or in collaboration with Compliance and Data Protection Officers, it is imperative you manage your company’s legal information to minimise legal risk created by cyber-attacks and data breaches.
Data breaches not only affect your company’s bottom line but if regulators and shareholders find that you breached various fiduciary duties by not mitigating known data security risks, you may also be at risk of personal liability. Therefore, GCs need a clear understanding of what makes them vulnerable so they can mitigate their risks and avoid liability.
While news headlines focus on the growing prevalence of cyber-attacks, much less malicious acts, like a lost computer or accidentally deleting a file, also cause data breaches. Therefore it is important to have a clear picture of the full gamut of threats you face.
Types of data security incidents that cause data breaches
We have identified the main sources of security threats that can result in a data breach classed as ‘Accidental’ or ‘Intentional’ breaches and those which are caused by Insiders (i.e. personnel) or Outsiders (i.e. hackers).
It may come as a surprise to learn that internal actors are responsible for 43% of data loss, half of which are intentional, half accidental. Accidental breaches by inside players can include lost documents or equipment (like mobile phones or laptops), sending data to the wrong person, unauthorised access to shared drives or corporate applications, and equipment failure (including computers, software or servers). People known to your company, like employees or partners, can also cause intentional breaches by stealing or leaking data in an attempt to profit from or sabotage the company.
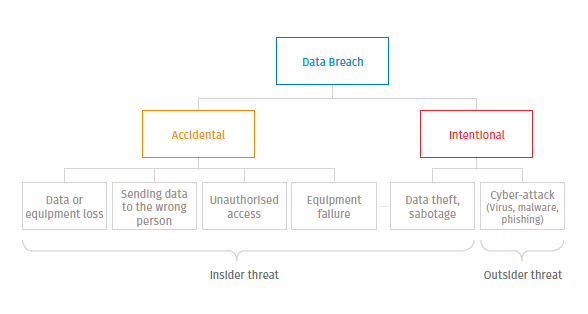
Outsider threats, on the other hand, are most often intentional and include attempts to steal your data by hacking or using phishing tactics to install malware – up by 870% in 2017 and becoming increasing more apt at disguising themselves as genuine.
So, while it pays to educate employees on how to mitigate the risk and making this part of your corporate policy, you want to have sophisticated technology in place in order to prevent data leaks or theft, as well as to detect when it has occurred and be able to trace it and act accordingly.
Preventing data breaches
Your best defence is to ensure your corporate data is encrypted and stored on a dedicated cloud-like Legisway where it is safe from viruses and corruption, backed up elsewhere and easily accessible. In the event that your local network system is compromised or equipment lost or stolen, data on the cloud is not only inaccessible to cyber-criminals, but you can keep working. It also lets you keep emails out of the equation when sharing data and properly manage access rights, so only the right colleagues can access certain data and all activity can be traced.





